Web Application Scanning by AmbiSure | Secure Your Apps Now
Web Application Scanning is critical for protecting your digital assets from today’s evolving threats. AmbiSure’s platform continuously scans your web apps, identifies vulnerabilities from a hacker’s perspective, and integrates real-time defense mechanisms to ensure security and compliance.
Overview
Don’t Let a Single Vulnerability Ruin Your Reputation.
Don’t wait for breaches to make headlines. With Web Application Scanning, you can detect and fix vulnerabilities before they’re exploited. AmbiSure’s dynamic scanning solution empowers enterprises to secure every layer of their web applications — fast, intelligently, and without disruptions.

The Challenge: Unseen Vulnerabilities
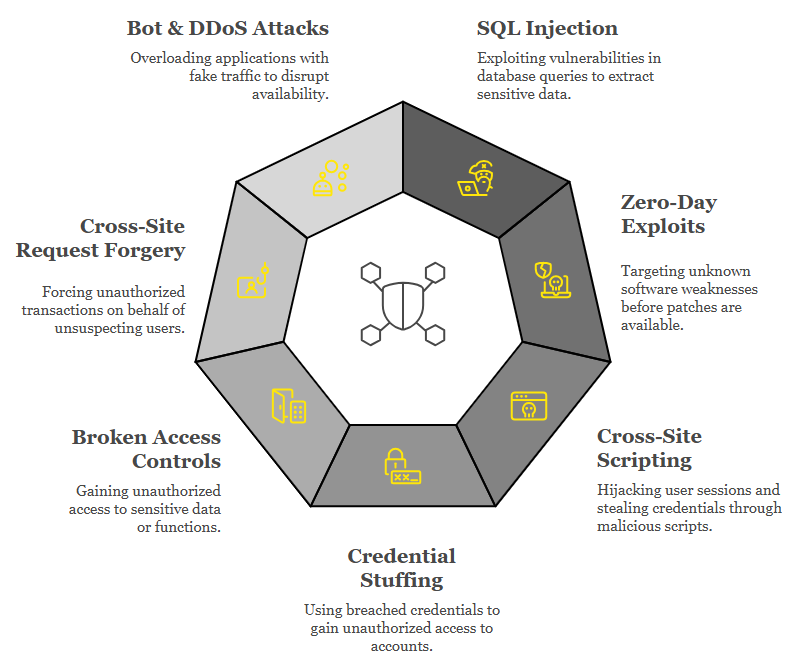
Applicable Threats
FEATURES
Technical Features & Significance
- Automated & Manual Scanning: Powered by both tools and human expertise.
- Risk-Based Vulnerability Prioritization: Focuses resources on what truly matters.
- Zero False Positives Promise: Saves time, avoids alert fatigue.
- DevSecOps Integration: CI/CD hooks to catch issues early in development.
- Managed Web Application Firewall (WAF): Constantly tuned for new threats.
- Real-Time DDoS & Bot Protection: Ensures availability of critical services.
- 24x7 Managed Support: Continuous security monitoring and updates.
Why it matters:
- Addresses OWASP Top 10 and PCI DSS gaps
- Reduces attack surface for BFSI, Pharma, Insurance, and Manufacturing sectors
- Boosts application trust and customer confidence
business benefits
Compliance Ready
Meets ISO 27001, GDPR, HIPAA, PCI-DSS, 21 CFR.
Reduces Cyber Risk
Cuts threat exposure by 85% within 30 days.
Boosts Operational Efficiency
Less firefighting. More prevention
Accelerates DevOps Velocity
By integrating security early in SDLC.
Enhances Application Trust
Protects brand reputation from breach headlines.
Supports Security Teams
Reduces alert fatigue and analyst workload.
Value Proposition:
CISOs and CTOs rely on AmbiSure for secure app development, real-time protection, and faster compliance. Our WAS Platform and 24x7 expert support delivers peace of mind and clear ROI.
Why Ambisure?
India’s Leading Cybersecurity Experts
With deep expertise in VAPT, CNAPP, Data Security, and DevSecOps.
Trusted by 40+ Global Security Brands
Authorized partners for cutting-edge solutions.
Regulatory Knowledge Advantage
Expertise with RBI, IRDAI, SEBI, HIPAA, FDA, and PCI mandates.
Zero-Hierarchy Delivery Model
Ensures faster, more personalized implementation and support.
Support Infrastructure Across Tier 1 & 2 Cities
Covers remote and critical installations seamlessly.
WHAT OUR CLIENTS SAY
"We reduced web application vulnerabilities by 90% within 60 days. AmbiSure's team is brilliant.""
— CISO, Leading Private Bank
"AmbiSure helped us sail through a surprise PCI audit. Their support is exceptional."
— Head of IT Compliance, Pharma Giant
"With AmbiSure, our DevOps and security teams finally speak the same language."
— CTO, Large Manufacturing Group
frequently asked questions
How is this different from a traditional vulnerability scanner?
- Most tools stop at scanning. Our WAS Platform combines automated scans with human-validated testing, risk prioritization, and managed firewall updates for complete lifecycle protection.
Can this integrate into our DevSecOps pipeline?
- Yes. The platform supports CI/CD tools through API integrations. It can trigger scans during builds and alert devs automatically.
Does this help with regulatory compliance audits?
- Absolutely. From PCI DSS to RBI/SEBI compliance, we offer audit-ready reports, mapped directly to control requirements.
What kind of support does AmbiSure provide?
- Dedicated technical account managers, 24x7 incident response, and remediation consulting. Our team handles both proactive and reactive needs.
How often is the WAF updated?
- Rules are updated daily and during zero-day events. Our team continuously tunes policies to reduce false positives.
Is this suitable for multi-cloud deployments?
- Yes. Works seamlessly across AWS, Azure, GCP, and hybrid models.
Can we customize rules and scanning parameters?
- Yes. You can define your own risk thresholds, policies, and scanning logic.
What if we don’t have internal security expertise?
- That’s exactly where we come in. Our managed model ensures expert help is always available.
