Privileged Access Management (PAM) by AmbiSure
Secure the Keys to Your Kingdom.
Eliminate Insider Threats. Enforce Least Privilege. Achieve Continuous Access Governance.
Overview
Your Privileged Accounts Are the Crown Jewels of Your Enterprise
Admin, root, and superuser accounts control everything—servers, databases, applications, and cloud environments.
If compromised, these identities can cause catastrophic damage: data theft, ransomware propagation, regulatory violations, and business disruption.
For CISOs, CIOs, and Compliance Heads in BFSI, Pharma, and Manufacturing, privileged access is the most targeted and the least controlled risk vector.
AmbiSure’s Privileged Access Management (PAM) solution delivers complete visibility, control, and governance over privileged accounts—across on-prem, cloud, and hybrid environments—enabling you to enforce least privilege, prevent credential misuse, and meet RBI, SEBI, IRDAI, and DPDP compliance mandates.

The Challenge: Unseen Vulnerabilities
CIOs, CISOs, CROs, and CTOs are under intense scrutiny. Key pain points include:
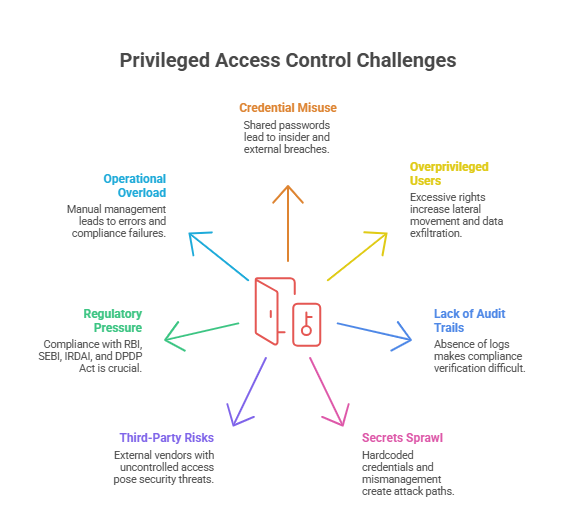
What If a Single Compromised Admin Account Could Bring You Down?
A leading insurance major prevented a major ransomware incident when AmbiSure PAM detected an unauthorized login to a domain controller from a remote vendor account. The automated session suspension and alert prevented privilege escalation—averting ₹12 crore in potential damage and data loss.
FEATURES
CART Features That Matter to You
-
Centralized Privilege Vault
Securely stores and rotates all privileged credentials, eliminating shared or static passwords. -
Just-In-Time (JIT) Access
Multi-Factor Authentication (MFA) Enforcement. -
Multi-Factor Authentication (MFA) Enforcement
Adds strong authentication to every privileged session, even for remote and third-party users. -
Session Recording & Command Control
Monitors, records, and audits all privileged sessions for accountability and compliance. -
Automated Password Rotation
Eliminates credential reuse by enforcing periodic rotation policies across endpoints and servers. -
Privileged Behavior Analytics (PBA)
Privileged Behavior Analytics (PBA) -
API & Secrets Management
Protects API keys, SSH keys, and DevOps secrets in hybrid cloud environments (AWS, Azure, GCP). -
Role-Based Access Control (RBAC)
Implements least-privilege policies aligned with Zero Trust principles. -
Third-Party & Remote Access Security
Provides secure, monitored access for vendors without exposing internal credentials. -
Compliance-Ready Reporting
Prebuilt dashboards and templates for RBI, SEBI, IRDAI, DPDP, ISO 27001, and GxP audits.
business benefits
Business Value Delivered by AmbiSure PAM
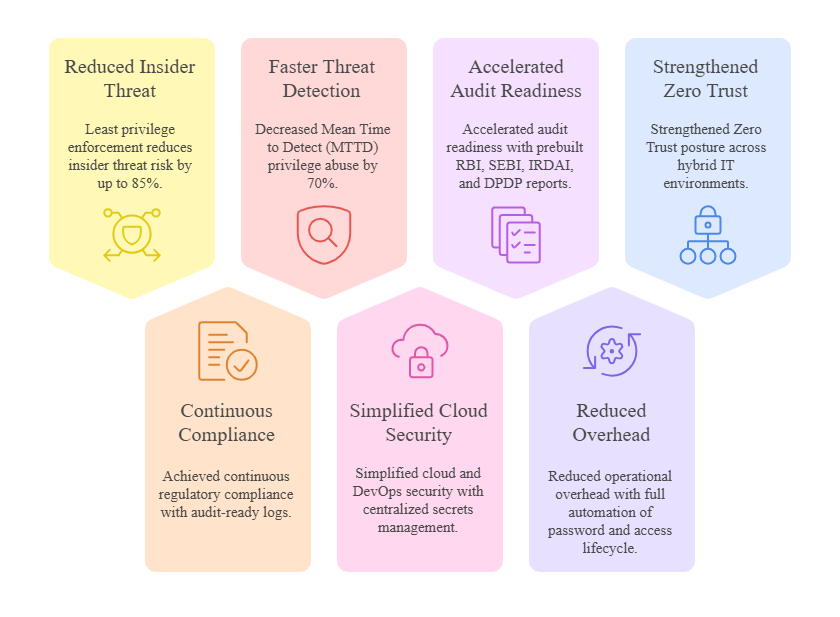
Real-World Use Cases
BFSI
Prevented unauthorized database access during core banking migration through time-bound privilege allocation.
Pharma
Protected GxP systems from third-party vendor credential misuse using secure remote access control.
Insurance
Automated privileged password rotation across 2,500 endpoints—eliminated shared admin logins.
Manufacturing
Stopped lateral movement of ransomware by enforcing least privilege and session monitoring.
Why Ambisure?
Regulatory Expertise
- Deep experience with RBI, SEBI, IRDAI, DPDP, and GxP frameworks.
End-to-End Implementation
- From strategy and deployment to continuous governance and optimization.
Zero Trust Alignment
- PAM designed as a foundation for Zero Trust Architecture and CTEM integration.
Rapid Deployment
- Get operational in under 2 weeks across hybrid infrastructures
24×7 Local SOC Support
- Continuous monitoring, alerting, and credential anomaly detection.
Proven Results
- Trusted by India’s top BFSI, Pharma, and Manufacturing leaders.
Advisory-Led Approach
- Beyond tools—strategic consulting to mature your identity security posture.
WHAT OUR CLIENTS SAY
“AmbiSure PAM gave us visibility into every privileged account across 40 applications—compliance audits became effortless.”
— CISO, Nationalized Bank
“We stopped shared password use overnight. The combination of MFA, JIT access, and session recording changed our entire security posture.”
— Head of IT, Pharma Major
“Ransomware stopped at the first hop. PAM’s least privilege model contained what could’ve been a disaster.”
— CTO, Manufacturing Giant
frequently asked questions
What does PAM protect against?
- Privileged Access Management protects against insider threats, credential theft, lateral movement, and data breaches stemming from admin misuse.
Does PAM integrate with Active Directory and cloud IAM?
- Yes. It integrates with AD, Azure AD, Okta, AWS IAM, and Google Cloud IAM.
Can it manage DevOps secrets and API keys?
- Yes. AmbiSure PAM includes Secrets Management for Jenkins, GitLab, Kubernetes, and CI/CD pipelines.
Is PAM suitable for third-party vendors and remote admins?
- Absolutely. Provides secure, monitored, and time-bound access without sharing credentials.
Does it support RBI/SEBI compliance reporting?
- Yes. Preconfigured templates and logs align with RBI Cybersecurity Framework, SEBI IT Security Guidelines, and DPDP Act.
Yes. Preconfigured templates and logs align with RBI Cybersecurity Framework, SEBI IT Security Guidelines, and DPDP Act.
- As on-premise, cloud, or hybrid model with high availability and scalability.
Can PAM detect suspicious privileged activity automatically?
- Yes. Privileged Behavior Analytics (PBA) continuously analyzes session activity for anomalies.
How fast can PAM be implemented?
- Typical enterprise rollout is 10–14 business days, with full automation and integration.
