Mobile App Security by AmbiSure – Enterprise-Grade Protection
Secure your mobile applications from evolving cyber threats with AmbiSure Technologies. Our Enterprise-Grade Mobile App Security solution ensures end-to-end protection, safeguarding user data, preventing breaches, and maintaining compliance — because your apps deserve nothing less than the best.
Overview
Secure Your Mobile Ecosystem with Confidence
Advanced threat actors are targeting mobile endpoints with sophisticated exploits. Enterprises need resilient, intelligence-led mobile security architectures. AmbiSure Technologies delivers a state-of-the-art Mobile App Security framework embedded with real-time defense mechanisms, runtime application self-protection (RASP), and zero-trust principles.

The Challenge: Unseen Vulnerabilities
Applicable Threats
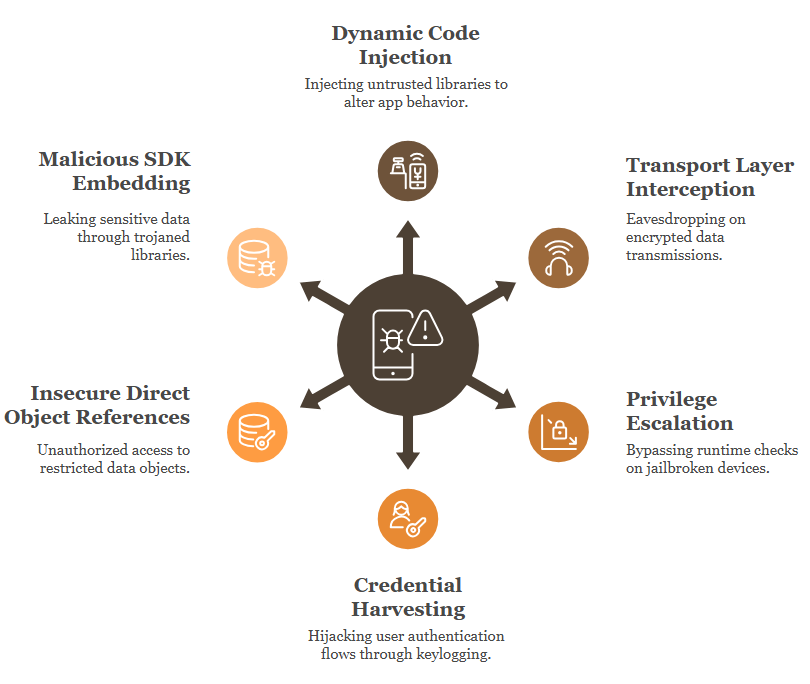
Gartner, Forrester, and Deloitte report a 64% YoY increase in mobile app-targeted APTs (Advanced Persistent Threats). They advocate adopting in-app runtime defense combined with centralized threat telemetry.
FEATURES
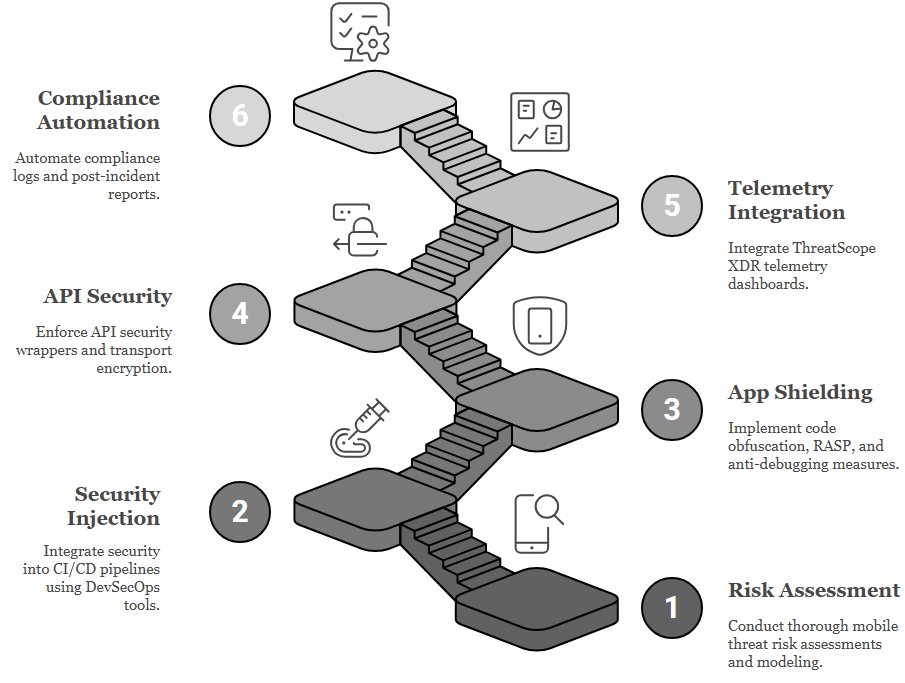
Technical Features & Significance
Advanced Protection Stack:
- Runtime Application Self-Protection (RASP): Dynamic memory inspection and behavior analysis at runtime.
- Multi-Layered Code Obfuscation: Encryption of logic branches, variable names, and control flows.
- Checksum & Signature Verification: Defends against tampering and binary replacement.
- Encrypted SQLite & SharedPreferences: Secures local mobile storage against root access.
- Mobile Threat Intelligence Feed Integration: Centralized insights from real-time attacks across app fleets.
- API Gateway Authentication Wrappers: Ensures mutual TLS and JWT-based token verification.
- Jailbreak and Emulator Detection Engines: Prevent app access from compromised environments.
- Compliance Dashboards & Forensics: In-built mapping to RBI, HIPAA, GDPR, SEBI, PCI-DSS audit readiness.
Integrated DevSecOps Pipelines:
- CI/CD security plug-ins compatible with Jenkins, GitLab, and Azure DevOps.
- Pre-release vulnerability scanning using DAST, SAST, and SCA modules.
- Post-deployment monitoring with ThreatScope (mobile XDR).
Future-Ready Innovations:
- Embedded anomaly detection using AI and Federated Machine Learning.
- Developer SDKs for custom alerting and embedded policy triggers.
business benefits
95% Reduction in Application Layer Exploits
Accelerated Compliance Audits via Built-in Reporting
Zero Downtime Security Patch Management
Real-Time Visibility Across All Mobile Endpoints
Enhanced End-User Trust via Frictionless In-App Protections
Centralized Attack Telemetry to CISO Dashboards
Target Teams:
CISO Office, DevSecOps, Application Development, Risk & Compliance, IT Governance
Why Ambisure?
AmbiSure Technologies – The Most Trusted Enterprise Security Partner

Enterprise-Grade Delivery
Successfully secured apps for 50+ BFSI, Pharma, and Manufacturing leaders.

Certified Engineers & Security Analysts
CREST, CEH, and CISSP certified team.

Local Compliance Mastery
In-depth understanding of Indian regulatory and IT compliance nuances.

Technical POCs & Threat Modeling Workshops
Custom validation before deployment.

24x7 SOC-backed Implementation Support
SLA-driven onboarding and lifecycle assistance.
WHAT OUR CLIENTS SAY
"We embedded AmbiSure’s runtime protection during our mobile banking app revamp. Audit timelines halved and incident rates dropped 92%."
— CISO, National Financial Services Provider
"Our Android and iOS apps are now threat-aware. AmbiSure helped us meet PCI-DSS mobile mandates effortlessly."
— Director IT, Pharma Manufacturing Group
frequently asked questions
Can this be integrated into enterprise CI/CD toolchains like Jenkins or Azure DevOps?
- Yes, the solution provides ready-to-use integration hooks for all major CI/CD systems with CLI interfaces and RESTful APIs.
Does this support multi-platform apps such as React Native or Flutter?
- Our platform secures native, hybrid, and cross-platform applications with platform-specific libraries and wrappers.
How does AmbiSure ensure data residency and regulatory mapping for Indian enterprises?
- We provide local hosting support, RBAC-enforced access, and compliance-specific configuration aligned with RBI/SEBI/HIPAA norms.
Can threat data be exported to our SIEM?
- Yes, threat logs and behavioral anomalies can be exported to Splunk, QRadar, or any SIEM over syslog or JSON format.
Is this compatible with BYOD environments?
- Yes, security is embedded at the application level, independent of device management, supporting MDM and unmanaged devices alike.
What’s the typical response time for zero-day threats?
- Threat telemetry enables under-2-hour turnaround time for new attack pattern mitigation.
Is real-time anomaly detection available without SDK embedding?
- Yes, our no-code solution allows real-time behavioral tracking without modifying the source code.
Do you provide UAT and developer training?
- Yes, AmbiSure offers technical training modules, developer handbooks, and code integration bootcamps.
