Continuous Automated Red Teaming (CART) | AmbiSure Cyber Threat Exposure Management
Attack. Adapt. Advance. Before Adversaries Do.
Expose Hidden Weaknesses. Validate Defenses. Strengthen Cyber Resilience.
Overview
Why Continuous Automated Red Teaming Matters More Than Ever
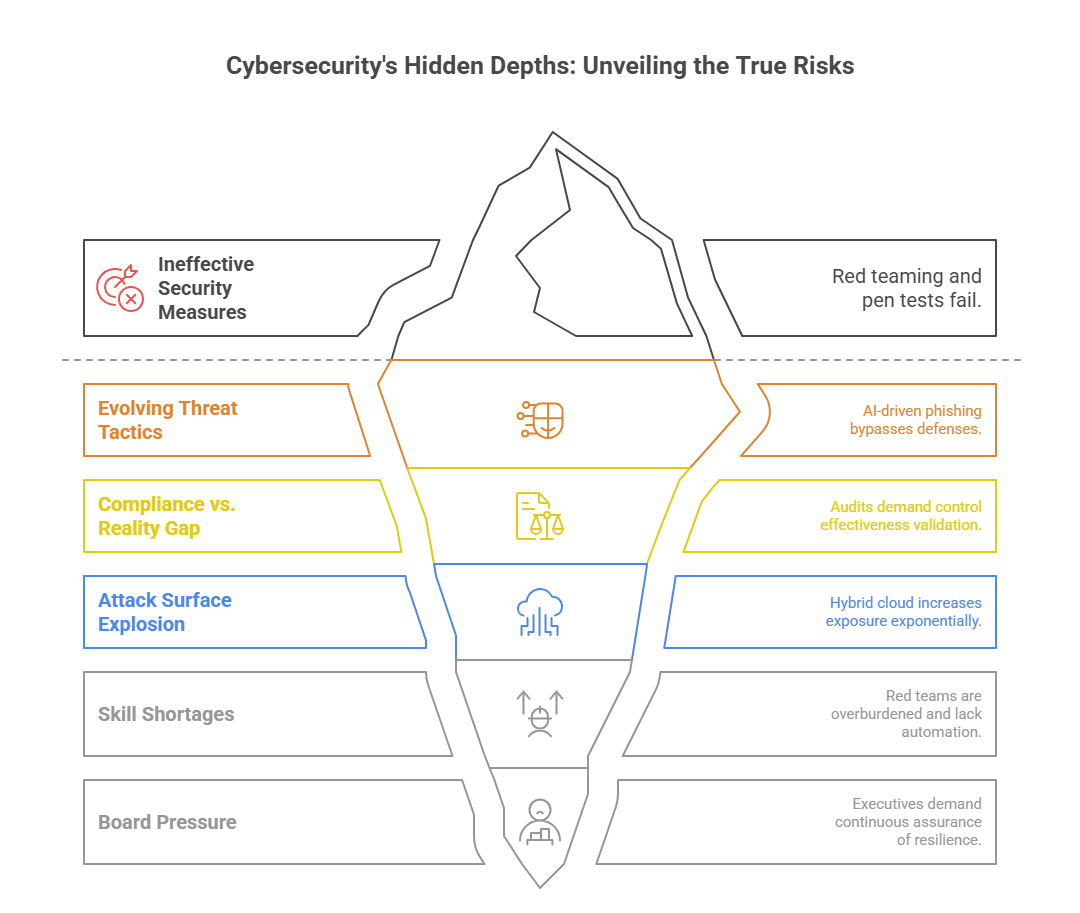
Threat actors don’t wait for your annual pen test.
They evolve daily—launching AI-powered, multi-vector, and zero-day attacks targeting critical assets across hybrid and cloud infrastructures.
For CISOs and CIOs in BFSI, Pharma, Insurance, Manufacturing, and Technology enterprises, traditional red teaming or one-off pentests no longer provide real assurance.
AmbiSure’s Continuous Automated Red Teaming (CART) transforms your security validation from a yearly checkbox to an always-on adversarial simulation engine, uncovering exploitable gaps before attackers do—continuously, safely, and at scale.

The Challenge: Unseen Vulnerabilities
CIOs, CISOs, CROs, and CTOs are under intense scrutiny. Key pain points include:
FEATURES
CART Features That Matter to You
-
Adversary Emulation-as-a-Service:
Simulates advanced persistent threats (APTs), ransomware, insider threats, and phishing campaigns—customized to your sector and threat landscape. -
AI-Powered Attack Scenarios:
Leverages machine learning to replicate dynamic adversarial behaviors aligned with MITRE ATT&CK®, D3FEND, and CISA Red Team frameworks. -
Continuous Validation:
Runs 24×7 automated campaigns to test endpoint, network, and cloud controls in real time—eliminating the “blind period” between tests. -
Exposure Mapping Dashboard:
Unified visibility into exploitable attack paths, control gaps, and defense drift across infrastructure layers. -
Safe Production Testing:
CART operates in a controlled, non-destructive mode—no service disruption, no data impact. -
Integration with CTEM Framework:
Feeds continuous results into Cyber Threat Exposure Management (CTEM) cycles for prioritization and remediation. -
Automated Reporting:
Generate CISO-ready dashboards for audits, board reviews, and regulator submissions—mapped to RBI, SEBI, IRDAI, and DPDP standards. -
Breach & Attack Simulation (BAS) Synergy:
Seamlessly integrates with BAS, SIEM, and SOAR tools like Microsoft Sentinel, Splunk, Palo Alto Cortex XSOAR, and ServiceNow for automated threat mitigation. -
Adaptive Attack Intelligence:
Updates tactics and payloads weekly with global and Indian-specific threat intelligence feeds. -
Gamified Defense Readiness:
Score your security posture, benchmark teams, and validate readiness metrics continuously.
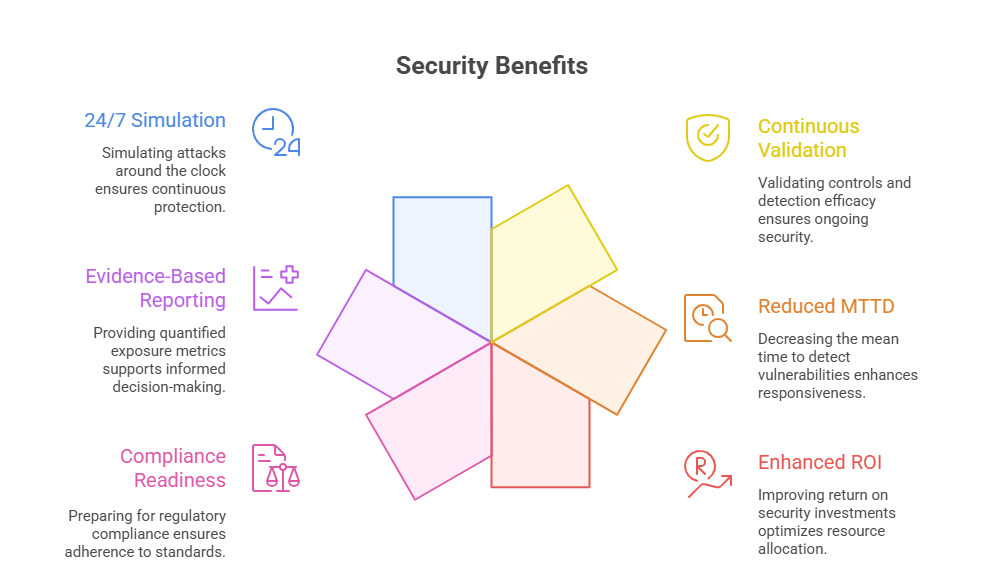
business benefits
Direct Benefits for CXOs:
Real-World Use Cases
BFSI
Continuous simulation of credential theft and data exfiltration attacks validated 92% EDR coverage and reduced unknown exposures by 67%.
Pharma
CART identified misconfigured cloud storage buckets during R&D trials—preventing IP data leakage.
Insurance
Tested response workflows under simulated ransomware and achieved a 45% faster containment rate.
Manufacturing
Exposed unmonitored OT network segments and insider privilege escalation vectors before real-world exploitation.
Why Ambisure?
CISO-Centric Engagement
- Designed to deliver measurable resilience metrics, not just attack data.
Regulatory Alignment
- Prebuilt templates for Indian compliance frameworks (RBI, SEBI, IRDAI, DPDP).
Adversarial Expertise
- CERT-In empaneled experts with decades of Red Team and Threat Intel experience.
CTEM Integration
- CART is a cornerstone of AmbiSure’s Cyber Threat Exposure Management suite, closing the loop from exposure to remediation.
Rapid Time-to-Value
- Go live within 7–10 business days, start simulations immediately.
India-Based 24×7 Support
- Local SOC and red team support ensure real-time guidance and rapid issue resolution.
Strategic Advisory
- Quarterly threat simulation reports, tabletop exercises, and CISO workshops.
WHAT OUR CLIENTS SAY
“CART exposed privilege escalation paths we never knew existed. The 24×7 visibility is a game-changer for our CTEM program.”
— CISO, Private Sector Bank
“AmbiSure’s automated simulations helped us uncover blind spots across multiple lab networks—no downtime, full visibility.”
— Head of Cyber Defense, Pharma Leader
“With CART, our red team went from reactive to strategic. We test, measure, and improve continuously.’’
— VP-IT Security, Manufacturing Giant
frequently asked questions
Is CART safe to run in production?
- Yes. All simulations are safe, controlled, and non-destructive—no impact on systems or data.
Does it replace manual red teaming?
- No. It complements human-led red teams by automating routine attack simulations continuously.
How does it integrate with CTEM?
- CART provides real-time exposure data to prioritize risks and validate remediation within CTEM cycles.
Can it test cloud and hybrid environments?
- Yes. CART covers on-prem, AWS, Azure, and GCP workloads.
Does it align with MITRE ATT&CK and RBI guidelines?
- Absolutely. CART maps every simulation to MITRE ATT&CK techniques and RBI cybersecurity controls.
Can we customize attack campaigns?
- Yes. Sector-specific threat scenarios and custom TTPs can be created easily.
Yes. Sector-specific threat scenarios and custom TTPs can be created easily.
- Typical onboarding in less than 10 working days.
Typical onboarding in less than 10 working days.
- Improved detection rates, validated control coverage, and faster incident response times—all visible in dashboards.
