BYOK + BYOE: Enterprise-Grade Data Sovereignty for Indian CXOs
Secure critical data, ensure compliance, and reduce breach impact — all without slowing down operations. CXOs trust AmbiSure for cloud-ready, regulation-compliant data protection.
Overview
Take Back Control of Your Cloud Data
Your keys. Your encryption. Your rules.
AmbiSure Technologies helps enterprises reclaim digital sovereignty with BYOK (Bring Your Own Key) and BYOE (Bring Your Own Encryption) solutions. Designed for India’s most regulated sectors, our enterprise-ready offering enables CISOs, CIOs, and CROs to mitigate third-party cloud risks, meet compliance mandates, and neutralize insider threats – without sacrificing cloud agility.
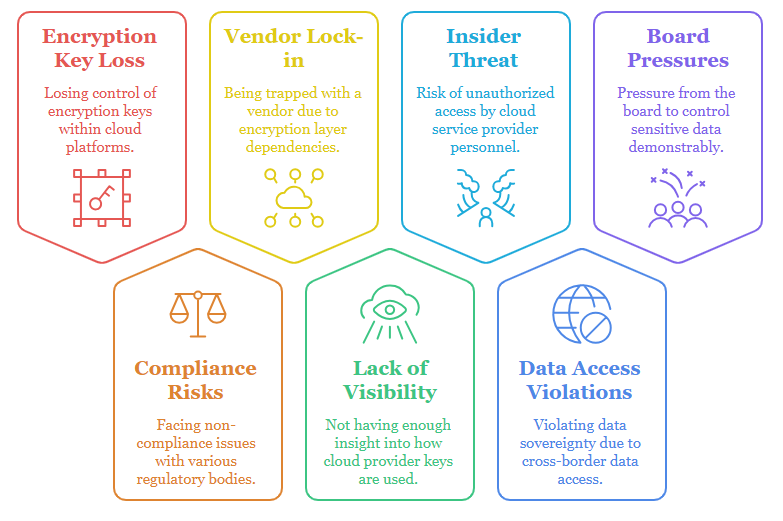
The Challenge: Unseen Vulnerabilities
Why CXOs Need BYOK + BYOE Today
FEATURES
What BYOK + BYOE from AmbiSure Offers
- Customer-Generated Keys: Keys created in your own HSMs or KMS.
- HSM Integration: Support for Thales, Entrust, AWS CloudHSM, Azure Managed HSM.
- Multi-Cloud Compatible: Works across AWS, Azure, Google Cloud, and private cloud.
- Zero-Trust Design: Encryption operations stay entirely within your control (BYOE).
- Audit-Ready Logging: Full logs of key access, rotations, and revocations.
- Encryption of structured and unstructured data before cloud upload.
- Granular key control by data classification level (PII, PHI, IP, etc.).
- Geographic control: restrict decryption to India-based HSMs only.
- Seamless revocation: Kill-switch capability for cloud-stored data.
- BFSI Core Banking Cloud Migration: Keep control of master keys even in shared environments.
- Pharma R&D Cloud Analytics: Encrypt genomic/IP data before upload; only decrypted on-prem.
- Healthcare Records in SaaS: Store ePHI encrypted with hospital-controlled keys.
business benefits
JUSTIFICATION FOR ENTERPRISE CXOs:

Achieve full compliance with DPDP, RBI Cybersecurity Framework, IRDAI norms.

Eliminate third-party decryption risk in cloud storage.

Reduce average MTTD/MTTR via full audit trails.

Prevent costly data breaches from cloud insider misuse.

Cut potential breach costs by 60% through externalized key control.

Minimize cloud exit barriers by owning encryption processes.
Why Ambisure?
Local Expertise in Indian regulatory mandates (DPDP, RBI, IRDAI, SEBI, Pharma GxP).




Direct relationships with OEMs of HSMs and KMS.
Indian support & deployment teams.






Trusted implementation partner to BFSI & Pharma majors.
Local Expertise in Indian regulatory mandates (DPDP, RBI, IRDAI, SEBI, Pharma GxP).



Direct relationships with OEMs of HSMs and KMS.



Indian support & deployment teams.



Trusted implementation partner to BFSI & Pharma majors.



What If You Were Breached Tomorrow?
Would you be able to revoke decryption instantly?
Yes. Because BYOK + BYOE implemented via AmbiSure, give you control of your encryption keys as well as data residency in India – inaccessible to the cloud provider.
Crisis Averted | Data Safe | Trust preserved.
WHAT OUR CLIENTS SAY
"BYOK solution helped us pass Regulatory audit without a single objection. The key sovereignty was the clincher."
— CISO, Financial Services
"We now upload sensitive genomic data to the cloud only after encrypting it with our own keys. AmbiSure made it simple."
— CTO, Insurance Major
"Our board wanted control and accountability on the data. We now show them real-time key usage logs."
— Head of Security, Broking Major
frequently asked questions
How does BYOK differ from cloud-native encryption?
- With BYOK, your enterprise generates and controls the keys. In cloud-native models, the provider controls them.
Can BYOK + BYOE be implemented across multiple clouds?
- Yes. AmbiSure supports AWS, Azure, GCP, and private clouds. Keys remain portable.
Will it impact cloud performance?
- Negligibly. Only certain encryption ops route to on-prem systems in BYOE. Key caching is optimized.
What happens if the key is lost?
- Data becomes permanently inaccessible. AmbiSure sets up key escrow and backup policies to avoid this.
Is this compliant with RBI and DPDP?
- Yes. In fact, BYOK + BYOE is often the only way to meet explicit mandates on key control and data localization.
How fast can this be implemented?
- Standard deployment takes 1 week post-sale. Expedited paths available for critical projects.
Will it support SaaS applications like Salesforce or Microsoft 365?
- Yes. We work with SaaS vendors that support BYOK APIs or layered encryption options.
