Your Encryption Is Only As Secure As Your Keys Are Managed.”
AmbiSure Technologies’ Key Management System helps organizations securely manage the lifecycle of cryptographic keys across digital workflows. From generation and distribution to rotation and revocation, every key is safeguarded with strong encryption, strict access controls, and detailed audit logs. Ensure every digital transaction, approval, or signature is protected by authenticated, tamper-proof encryption—enhancing security, ensuring compliance, and supporting scalable, streamlined operations.
Overview
The Silent Risk Haunting Every CXO Boardroom
BFSI. Pharma. Manufacturing. Insurance. The stakes are towering.
Your organization encrypts terabytes of mission-critical data daily. But ask yourself:
- Where exactly are your encryption keys stored?
- Who can access them today?
- Can you rotate them instantly when mandated?
One compromised key can trigger data breaches, regulatory penalties, reputational collapse, and even board-level accountability.
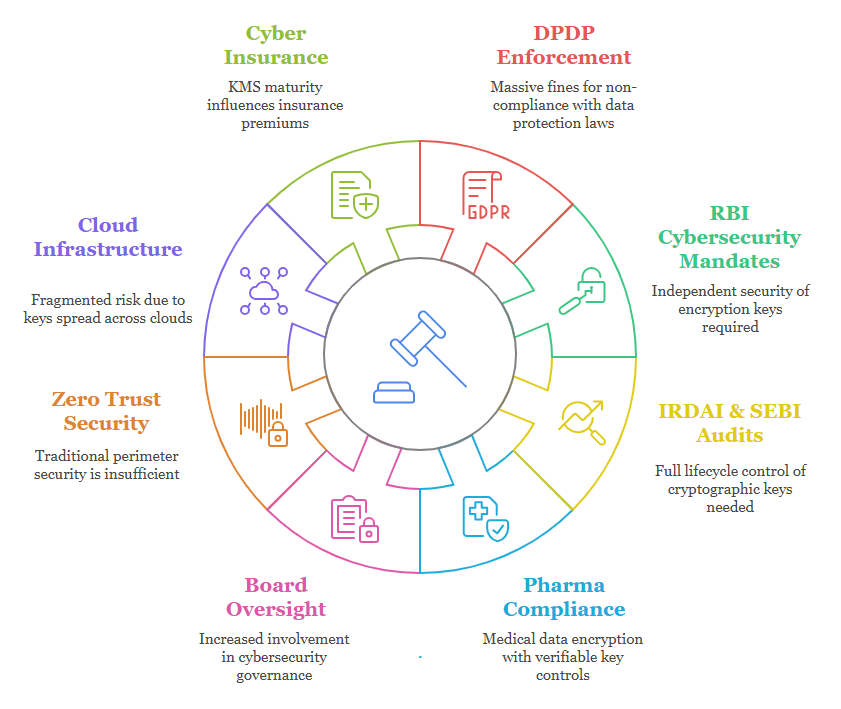
India’s DPDP Act, RBI Circulars, SEBI Guidelines, IRDAI Mandates, and Pharma GxP standards all demand uncompromised key management.
Without an industrial-grade Key Management System (KMS), your encryption strategy is incomplete.
The Challenge: Unseen Vulnerabilities
The Business Challenges Forcing Enterprises to Act
As per Gartner 2024: “By 2026, 70% of large enterprises will mandate centralized KMS as part of their data governance strategy.”
FEATURES
The KMS Capabilities That Secure Boardroom Confidence
AmbiSure’s KMS offering, backed by our Preferred Value-Added Partnership, delivers:
1. Centralized Key Lifecycle Management
- Key creation, rotation, archival, and destruction.
- Avoids key sprawl across multiple environments.
2. Hardware Security Module (HSM) Integration
- FIPS 140-2/3 validated HSM protection for master keys.
- Keys never leave the secure hardware boundary.
3. Regulatory Audit Readiness
- Full audit logs of every key access, change, and usage.
- Satisfies RBI, DPDP, SEBI, IRDAI, PCI DSS, 21 CFR Part 11, HIPAA, GDPR audits.
4. Granular Access Control
- Role-based access control (RBAC), multi-party authorization.
- Split-key custody for critical functions.
5. Multi-Cloud & Hybrid Support
- Unified key management across AWS KMS, Azure Key Vault, Google KMS, On-Prem, SaaS.
- Prevent vendor lock-in.
6. Key Usage Policy Enforcement
- Define which systems, apps, and APIs can access keys.
- Prevent unauthorized encryption/decryption operations.
business benefits
JUSTIFICATION FOR ENTERPRISE CXOs:
BFSI: Preventing a ₹25 Cr Regulatory Penalty
A major Indian bank faced an urgent RBI audit gap. With AmbiSure’s KMS, they achieved:
- Full key lifecycle audit visibility.
- Immediate rotation on suspected compromise.
- Automated compliance reporting.
- Audit closure within 60 days.
- Full key lifecycle audit visibility.
- Immediate rotation on suspected compromise.
- Automated compliance reporting.
- Audit closure within 60 days.
Pharma: Passing GxP Compliance With Confidence
One of India’s top pharma manufacturers faced US FDA scrutiny.
- Deployed KMS integrated with Electronic Lab Notebooks (ELNs).
- Ensured patient data encryption with controlled key custodianship.
- Zero non-conformities flagged in subsequent audit.
- Deployed KMS integrated with Electronic Lab Notebooks (ELNs).
- Ensured patient data encryption with controlled key custodianship.
- Zero non-conformities flagged in subsequent audit.
Manufacturing: Insider Threat Containment
A global auto component firm neutralized insider risk:
- Data encrypted with KMS-controlled keys.
- No admin or DBA had direct key access.
- Attempted unauthorized access fully blocked and logged.
- Data encrypted with KMS-controlled keys.
- No admin or DBA had direct key access.
- Attempted unauthorized access fully blocked and logged.
Why Ambisure?
Compliance Enablement
- DPDP, RBI, IRDAI, SEBI, PCI DSS, HIPAA, GDPR ready.
Regulatory Audit Readiness
- Pass audits with complete, verifiable key usage logs.
Operational Cost Optimization
- Reduce manual key rotation costs by up to 80%.
Vendor Independence
- Interoperable across clouds & infrastructure.
Business Continuity Assurance
- No single point of failure. Highly available multi-site architecture.
Incident Response Acceleration
- Rapid key revocation and crypto-shredding capabilities.
WHAT OUR CLIENTS SAY
"AmbiSure helped us achieve RBI compliance in record time. Their KMS deployment became our cybersecurity anchor."
— Group CISO, Leading Private Bank
"With AmbiSure’s KMS, our pharma plants passed multiple GxP audits without a single non-conformance."
— Global Head IT Compliance, Indian Pharma Major
"Our key exposure risk reduced by over 90%. The insider access controls are industry-leading."
— CIO, Global Manufacturing Group
frequently asked questions
Will KMS disrupt our current operations?
- No. AmbiSure follows a phased integration with zero production downtime.
What is the ROI for KMS?
- Most clients recover investment within 12-18 months via audit savings, risk reduction, and operational efficiency.
Will my board understand this investment?
- Yes. We provide Boardroom Justification Packs tailored for CFO, CIO, CISO, and Audit Committees.
Can it integrate with our multi-cloud platforms?
- Fully supported across AWS, Azure, GCP, SaaS, and on-prem environments.
Will we be vendor locked?
- No. Our KMS supports BYOK, HYOK, and open APIs for maximum flexibility.
How does it handle high-volume transactions?
- Optimized for millions of cryptographic operations per second with no latency degradation.
Who manages the keys?
- You retain full control. Split custody and role-based access prevent misuse.
Is AmbiSure certified to implement this?
- Yes. Certified to handle regulated environments in BFSI, Pharma, Insurance, and Manufacturing.
