HSM: The Preferred Cyber Defense Anchor for India’s Largest Enterprises
AmbiSure Technologies’ Secure Digital Workflow leverages Hardware Security Modules (HSMs) to protect every step—approvals, e-signatures, routing—with tamper-proof encryption, strong authentication, and complete audit trails. Boost productivity with end-to-end security and compliance built in.
Overview
Don’t Let Keys Become Your Weakest Link: Bulletproof Enterprise Cryptography with HSM
In complex enterprise ecosystems, encryption keys are your crown jewels. But where do you securely store and manage them? AmbiSure brings you HSM — Hardware Security Module — the most desirable cryptographic vault for India’s largest enterprises.
We’re not just talking security. We’re talking uninterrupted business, regulatory compliance, and digital trust — executed with surgical precision.
The Challenge: Unseen Vulnerabilities
Business Challenges
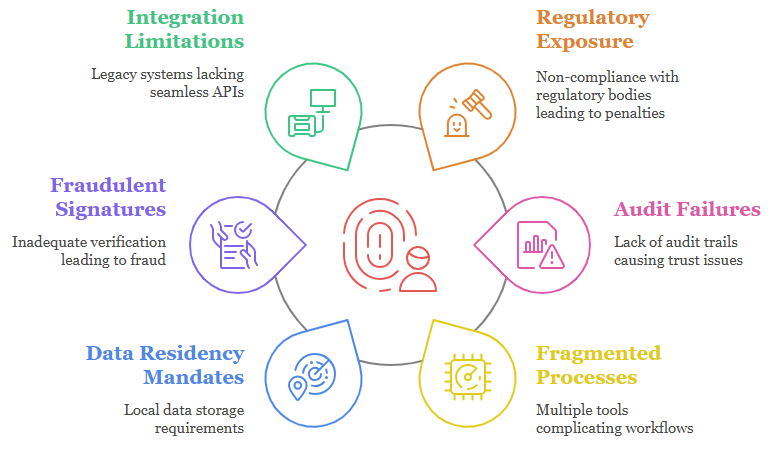
According to Gartner 2025:
"Organizations that don’t externalize key protection to certified HSMs will fail 80% of future audit and regulatory checkpoints."
HSM directly addresses these fears — minimizing risk and maximizing trust.
FEATURES
TECHNICAL FEATURES & SIGNIFICANCE
"Engineered for CXO Peace of Mind"
1. Multi-Deployment Flexibility: On-Prem, Cloud & Hybrid
Supports Thales Luna, Utimaco CryptoServer, Entrust nShield, Futurex, and JISA CryptoBind platforms.
Multi-cloud integrations: AWS KMS External Key Store, Azure BYOK, Google External KMS.
Native API-first integration with DevOps pipelines & application workloads.
2. Multi-Tenancy & Virtualization
Logical partitioning up to 100 isolated HSM instances.
Containerized secure environments for segregated business units.
Meets multitenant enterprise or shared service models perfectly.
3. Certified Compliance — Regulatory Shield
FIPS 140-3 Level 3
PCI PTS HSM v3.0
Common Criteria EAL4+
eIDAS QSCD compliance
RBI Gopalakrishna Committee, SEBI Cybersecurity Framework, SWIFT CSCF, DPDP Act alignment
4. Performance for Modern Cryptography
50,000+ TPS for payment HSM operations (e.g. PIN translation, CVV validation, EMV data prep).
20,000 ECC signatures/sec for blockchain, TLS offloading, PKI issuance.
Post-Quantum Cryptography ready.
5. DevSecOps-Ready Integration
Supports PKCS#11, KMIP, JCE, Microsoft CNG.
RESTful API and SDKs across Java, C/C++, Python.
HashiCorp Vault integrations for CI/CD.
USE CASES:
- Real-time payment processing (UPI, NEFT, IMPS, RuPay)
- Digital onboarding and eKYC secure signing
- Card issuance & personalization
- Secure IoT device identity management
- Database encryption & tokenization
- SWIFT key protection
- Blockchain and crypto custody
- Software code signing pipelines
business benefits
JUSTIFICATION FOR ENTERPRISE CXOs:
"Quantifiable Value Delivered"
Risk Elimination:
- Zero-key exposure architecture
- Insider threat nullification with tamper-proof hardware
Compliance Assurance:
- Automates compliance audits
- Instantly meets RBI, IRDAI, HIPAA, PCI-DSS mandates
Cost Optimization:
- Consolidates multiple crypto roles in one appliance
- Reduces hardware sprawl via virtualization
Business Continuity Focused:
- No crypto outage during DR events
- Multi-region HA/DR replication
Competitive Advantage:
- Faster onboarding of digital services
- Stronger customer trust through verified digital identities
Proactive Security Posture:
- PQC preparedness
- Hardware Root of Trust for future cyber resilience
Why Ambisure?
"We Deliver What Vendors Alone Cannot"
Product Agnostic Expertise
We represent the full HSM spectrum — Thales, Utimaco, Entrust, Futurex, JISA.
Regulatory Navigation
We interpret RBI, SEBI, IRDAI, DPDP, and global standards for you.
Seamless Deployment
Our team has real deployment experience across BFSI, Pharma & Manufacturing.
Seamless Deployment:
Our team has real deployment experience across BFSI, Pharma & Manufacturing.
Rapid Integration
Pre-built connectors, cloud hooks, and DevSecOps bridges.
Local Sovereignty:
Indigenous CryptoBind HSM options for national data sovereignty demands.
WHAT OUR CLIENTS SAY
"What CXOs Say After Deploying HSM with AmbiSure"
"AmbiSure didn’t just deliver hardware. They delivered control. In a sector driven by regulatory audits, this partnership made our compliance zero-headache."
— CISO, Leading BFSI Giant
"With AmbiSure's help, we secured not just our IP but the very DNA of our manufacturing — our intellectual assets are now fully protected across multi-clouds."
— CTO, Top 5 Pharma Company
"We moved to Industry 4.0 — and AmbiSure’s HSM architecture ensured our operational integrity even during supply chain cyber disruptions."
— CIO, Fortune 500 Manufacturing Group
frequently asked questions
Will HSM add operational complexity?
- No. HSM simplifies by consolidating cryptographic operations centrally with automated policy enforcement. Management GUIs and SDKs provide operational ease across diverse teams.
What happens if HSM fails? Does it affect business continuity?
- HSMs are deployed in clustered HA/DR setups. Failover occurs seamlessly without service disruption. Recovery keys are securely mirrored across geographies where allowed.
Can my legacy systems integrate into HSM architecture?
- Absolutely. HSM supports PKCS#11, KMIP, CNG, and JCE standards. Legacy systems from mainframes to core banking to ERP are supported.
How does this impact my RBI & DPDP Act audits?
- HSM eliminates audit risk by enforcing hardware-bound cryptographic control, satisfying both data localization and privacy controls.
What if we migrate cloud providers?
- Key material remains under your full control. HSM supports BYOK, BYOE, and cloud-neutral KMS integrations ensuring zero vendor lock-in.
Will this protect against insider threats?
- Yes. Private keys never leave the hardware boundary. Admin access requires dual control, multi-factor authentication, and audit logging.
Can this handle quantum computing risks?
- Yes. Future-proof firmware upgrades allow PQC algorithms as standards mature, keeping your crypto posture resilient.
How long is the implementation cycle?
- With AmbiSure — typically 4 to 6 weeks for full deployment, including customization, integration, and staff training.
