Breach Attack Simulation & Exposure Validation | AmbiSure India
AmbiSure’s Adversarial Exposure Validation (BAS/EVP) continuously emulates real-world cyberattacks across your IT, cloud, and OT systems—exposing exploitable gaps before adversaries do.
Overview
“Don’t wait for a breach to find your weakest link.”
Indian enterprises face relentless ransomware, phishing, insider threats, and evolving attack vectors. Traditional audits and annual penetration tests are no longer enough.
For BFSI, Insurance, Pharma, and Manufacturing giants (₹5000+ Crore turnover), this means quantifiable assurance, compliance readiness, and protection of shareholder trust.

The Challenge: Unseen Vulnerabilities
CIOs, CISOs, CROs, and CTOs are under intense scrutiny. Key pain points include:
Audit & Regulatory Pressure
RBI, SEBI, IRDAI, DPDP Act, and Pharma GxP demand evidence of continuous control validation. Fines for audit failures can cross ₹20–50 Crore.
Boardroom Accountability
Shareholders expect CISOs to present measurable cyber risk metrics, not assumptions.
Long Detection Times
Industry reports (IBM, Verizon DBIR) show breaches in India often go undetected for 180–220 days.
Tool Inefficacy
Enterprises invest millions in SIEM, EDR, WAF—but often discover post-breach that controls failed silently.
Shortage of Skilled Staff
In-house red teams are expensive and hard to retain. CXOs can’t rely solely on manual, point-in-time tests.
Operational Disruption Risks
Breaches risk downtime of critical BFSI systems, pharma R&D labs, or manufacturing plants—impacting revenues and brand equity.
Escalating Insurance Premiums
Cyber insurers are raising premiums for firms without continuous exposure validation.
FEATURES
DWM Features That Matter to You
- Automated Attack Simulation Engine: Safely replicates thousands of real-world TTPs (MITRE ATT&CK mapped) across endpoints, cloud, applications, and OT networks with Industry’s largest & most up-to-date attack repository.
- Continuous Exposure Validation: Goes beyond vulnerability scans by confirming which exposures are exploitable and what business impact they cause.
- Threat Intelligence Integration: Aligns simulations with the latest RBI/CERT-In advisories and global APT tactics.
- No-Code Red Teaming: Drag-and-drop interface empowers your SOC to simulate sophisticated attacks without scripting.
- Compliance Reporting: Maps results to RBI, SEBI, IRDAI, DPDP, ISO 27001, PCI-DSS, and Pharma GxP controls for audit evidence.
- Customisation: Create & simulate your own attack playbooks
- FBI or US – CERT alerts: Feel confident of attack coverage with new attack playbook available tobe simulated within 24 hours of CERT alerts.
- Attack Path Analysis: Shows how an attacker could move from initial breach to crown jewels.
- Tool Efficacy Validation: Confirms if SIEM, SOAR, EDR, and DLP are actually catching threats.
- Boardroom Dashboards: Risk exposure and remediation impact presented in simple, executive-ready visuals.
business benefits
Direct Benefits for CXOs:
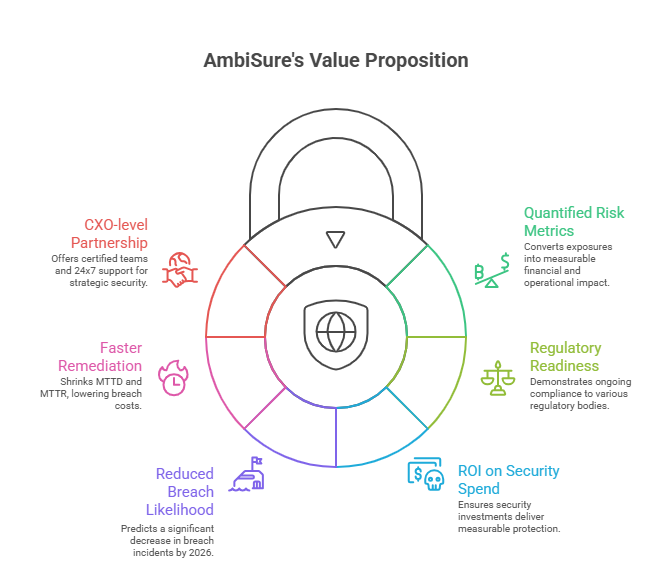
Real-World Use Cases
BFSI
A BFSI firm validates if ransomware could bypass layered defenses and reach payment systems.
Pharma
A Pharma company simulates insider credential theft to check data leakage from clinical trial databases.
Manufacturing
A Manufacturing giant tests if OT/IoT production line devices can be exploited to halt operations.
WHAT OUR CLIENTS SAY
“AmbiSure’s exposure validation gave us boardroom-ready risk metrics. For the first time, I could show the Audit Committee measurable resilience improvements.”
— CISO, Leading Private Bank
“Simulations revealed a misconfigured server path that could have leaked sensitive R&D data. Fixing it saved us millions in potential compliance penalties.”
— CTO, Top Pharma Company
“Our insurance renewal premium dropped after adopting BAS. The insurer recognized our continuous validation as reduced risk.”
— CRO, Manufacturing Giant
frequently asked questions
How safe are these attack simulations in production?
- All simulations are non-destructive, using safe payloads and controlled processes to avoid business disruption.
How is this different from traditional VAPT or penetration testing?
- Unlike one-off tests, BAS/EVP provides continuous, automated, evidence-based validation of exposures across the year.
Can this replace my red team?
- It complements red teams by automating routine scenarios and freeing them to focus on advanced, creative attacks.
How does it support regulatory audits?
- Reports are mapped to RBI, SEBI, PCI DSS, ISO 27001, DPDP Act controls—ready for auditor submission.
What if I already have SIEM, SOAR, EDR tools?
- BAS proves whether these tools detect and stop real-world attack scenarios—maximizing your cyber ROI.
How soon can we implement?
- Deployment is typically completed in under one week post-purchase.
Will it overwhelm my SOC team with data?
- No. It filters vulnerabilities down to those truly exploitable, cutting false positives by ~37%.
What’s the ROI for my enterprise?
- Enterprises typically see reduced incident costs, faster audits, and up to 50% lower breach probability within 12 months.
